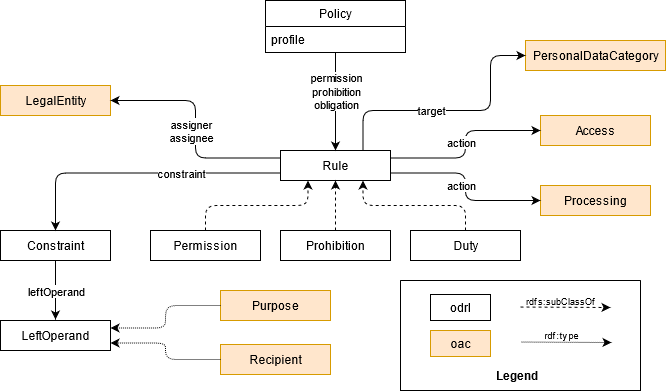
Motivation
Legal compliance
a) Document activities and maintain provenance regarding personal data processing, requests for access, notices and subsequent use logs to conduct a GDPR Data Audit;b) Determine applicable rights, obligations, and requirements based on jurisdictional laws or contextually e.g. specific categories of personal data;
c) Evaluate, assess, or validate if obligations and requirements are fulfilled;
d) Implement GDPR security requirements.

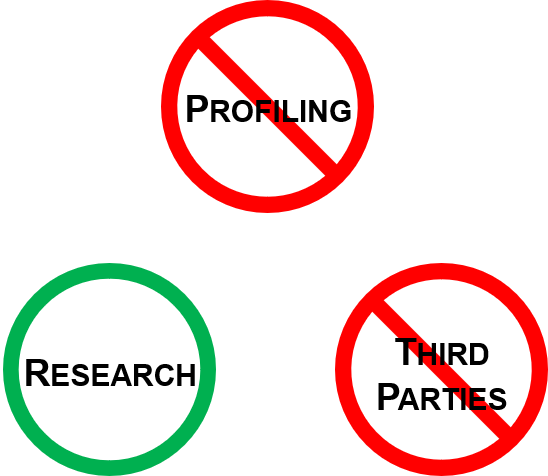
User-defined preferences for data sharing and use
a) Express human-centric preferences e.g. willingness to share particular data for research, or prohibition of profiling and surveillance;b) Granularity for specifying broad permissions, e.g. permit data use for scientific research, or prohibit any third party data collection;
c) Granularity for specifying narrow permissions, e.g. permit sharing contact details for a specific app, prohibit accessing a confidential resource;
d) Conflict resolution going from local to global, e.g. generally prohibiting sharing of location, but making an exception for specific services.
Transparency of data practices
a) Individuals want to know who is using which data categories, for what purposes, sharing it with whom, and under what legal basis;b) Individuals want to understand permissions/authorisations they already have provided based on self-defined context, e.g. for specific services or organisations, or based on purposes, or categories of personal data;
c) Organisations may want to specify their data policies in machine-readable forms that can be accessed by users.